The OSI Virtual Machine Model
The term "virtual machine" can conjure up a wide range of images for many people. The term "virtual" is commonly used by the popular media and news broadcasts in reference to new developments in computer simulations and computer gaming programs. In either case, "virtual" is used to imply that an object or device is observable without physically existing at that time and place. This use of the term virtual is a reasonable assumption concerning the development of an extended virtual machine. The creation and continued development of an extended virtual machine is a logical growth of computer operating systems in both ability and versatility.
|
..."virtual" is used to imply that an object or device is observable without physically existing at that time and place.
|
The need to understand how a modern computer is designed and manipulated
by an operating system is key to comprehending the extended virtual machine
model. Modern operating systems consist of sets of instructions combined
into service routines. These service routines are combined with data into
programs that are entered into the computer as application programs. The
combining of instructions into service routines is analogous to combining
the simple actions of an office clerk to perform a more complex task such
as an inventory of office supplies. For example, the file clerk could have
a limited set of basic instructions that he can perform from memory. These
instructions might be as limited as counting something, record result of
a previous operation, and file or store some information for later use.
These instructions used individually are of limited value. However, the
instructions could be combined in a sequence of instructions to direct
the office clerk to perform and inventory of office supplies. The sequence
of instructions could look something like: count note paper, record result,
count pencils, record result, count paper clips, record result, file results
for storage. This sequence could then be used over repeatedly to perform
the inventory service when ever it was requested. The use of instructions
such as "count note paper" does assume that the office clerk has certain
"built-in" abilities, such as recognizing note paper and counting it properly.
In a human office clerk this ability to recognize objects and count is
a natural function of the clerks brain and eyes. In the simulated office
clerk or computer these functions would be designed and built into the
computer circuitry the at the hardware level. The need to implement some
basic frequently used functions in circuitry instead of combining simpler
instructions is apparent when examining the office clerks actions in detail.
The office clerk has to physically move around the office, visually detect
objects, use a note pad and pencil to record counts etc. These functions
would be implemented as repeated sequences of hardware actions and software
instructions. For example, the instruction "record result of last operation"
would involve accessing a storage device such as a disk drive, locate space
to record data, retrieve the data to be recorded from local registers,
transferring the data, and writing it to the space on the hard disk. There
has to be a basic level where all the instructions originate at the circuit
level.
The most basic instruction is when a pattern of ones and zeros is presented
to the computer and produces an action to move data, configure the system
or set up a condition for needed for the next action. This level can be
considered the machine instruction level from which the operating system
level instructions are made. It should be clear now that any instruction
set is simply a combination of lower level instruction sets. The office
clerk is performing tasks that are really a series of sub tasks strung
together to form a more complex sequence of actions. When the instruction
"inventory" is given to the office clerk an observer perceives only the
meaning of the word inventory and the associated action of the office clerk.
The underlying sub sets of instructions are hidden from the observer. Each
successive layer of instructions, machine circuitry, machine code, operating
system instructions, and application program code, hides the underlying
levels of instructions from the next user. This ability to combine instructions
and construct more complicated actions is a key concept in understanding
the extended virtual machine. 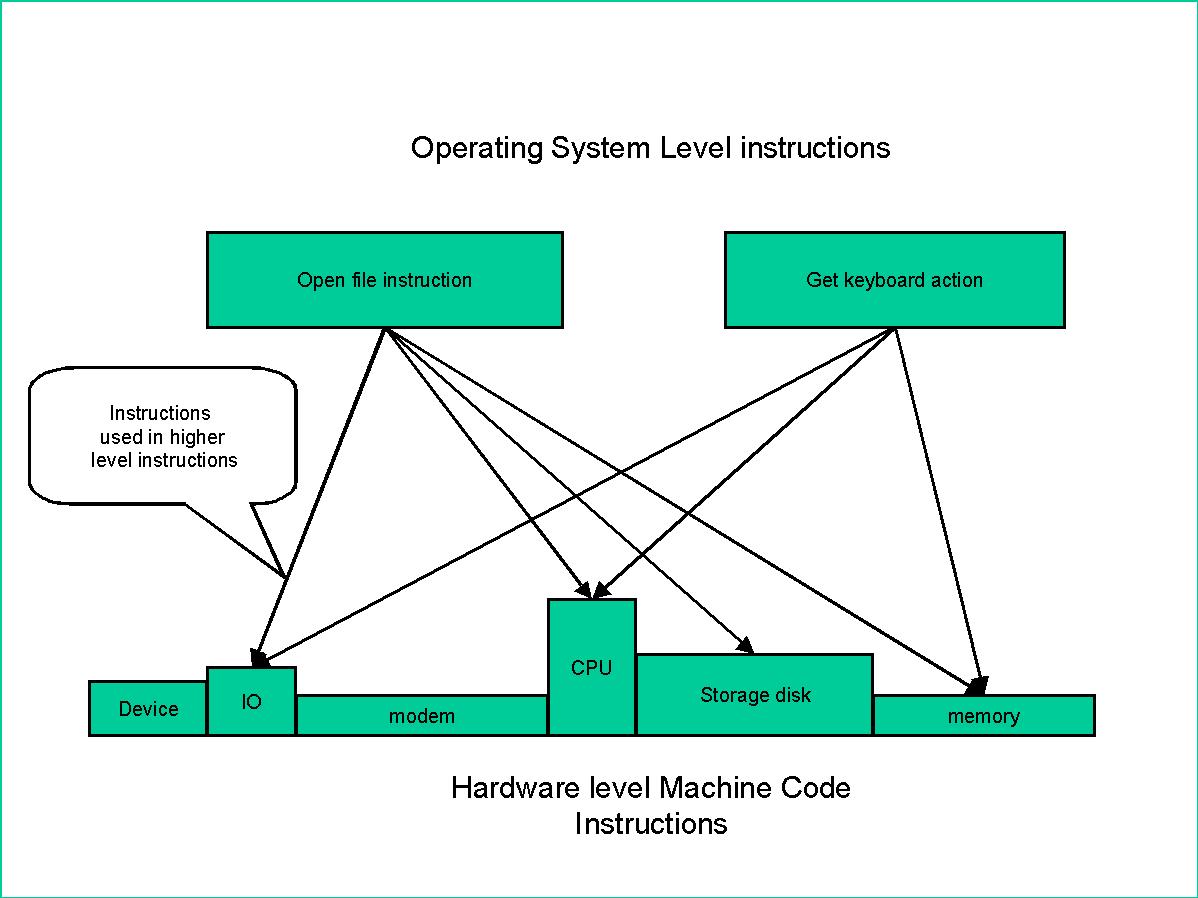
The eventual goal of the extended virtual machine is to build capabilities
and simulated devices that do not actually exist physically in the computer.
For example, most computers have a hard disk for storing data and program
instructions. The hard disk may in fact be located on a different computer
or consist of multiple drives attached to the same computer. An extended
virtual machine approach to this situation could be to program sequences
of instructions to present the user with the appearance that there is only
one hard disk drive attached to the computer. The single simulated hard
drive would have a storage capacity equal to all the attached hard drives.
The user would see only one hard drive through the computer and simply
use the combined instructions to store and retrieve data as if there was
one large hard drive available. The instructions called by the user access
sub routines that are combinations of lower level instructions that handle
the details of tracking what information was stored on which hard disk.

|