Workflow in the Web
Peter J. Denning
George Mason University
3/18/96
© Copyright 1996 by Peter J Denning and Future Strategies, Inc.
This work appeared as a chapter of the book New
Tools for New Times: Electronic Commerce, Layna Fischer, Ed., Future
Strategies, Inc. (1996), 45-57. You may make one hard copy of
this document for your personal
use only. Any other copying, storage, or use for any purpose and in any
form requires permission.
The Coming
In 1985, the Internet was a collection of networks connected by gateways
with a common protocol that allowed about 10,000 host computers to exchange
email, transfer files, and remotely log in. Most of the communications and
many of the host computers were paid for by government; the Internet was
used exclusively for education, research, and government communications.
Scarcely anyone imagined that, ten years later, the networks would be open
for commerce, that Internet would be a household word, that people would
routinely show their email addresses on their business cards, that desktop
operating systems would include World Wide Web browsers, that home computers
would be part of Internet, that advertisements in newspapers or TV would
carry "http" addresses, or that it could be profitable to operate
a business to help other companies set up "web presences".
Yet this is exactly what happened. No one knows how large the Internet is
any more; estimates at the start of 1996 placed it at approximately 10 million
computers and 50 million users -- and growing at 30-50% per year A quarter
of those computers are in commercial firms. O'Reilly & Associates said in
March 1996 that 51% of large companies and 25% of medium companies have
Internet access; they expected that by 1997 these numbers would rise to
65% and 40% respectively. O'Reilly also said that 35% of the large and 20%
of the medium companies had public web sites. Meanwhile, investors drove
Netscape stock from an initial opening of around $15 to over $150 in three
months in 1995, and CyberCash from a similar start to $50 in one week in
1996. The Internet is hot.
Business people are attracted to the promise of the Internet, which can
expand their reaches in many ways. With the Internet, it is said, you can
advertise to the world at lower cost than the local newspaper, you can be
your own publisher without a middleman, you can lower your advertising budget,
you can set up a mall without getting permission from a zoning board, you
can accommodate many visitors to your mall without a large sales force,
you can create a market niche too small for your local neighborhood but
sustainable in the "global village," you can cross time zones
and language barriers at will, and in doing all this you hardly pay more
for a call to the other side of the world than to next door.
"Electronic commerce" has become a popular term for carrying out
these and other business functions in the Internet. A host of Internet technologies
make this all feasible: self-publication of Web pages, attaching order forms
to Web pages, electronic mail, payment systems, digital cash, and powerful
search engines that will find anything advertised in the Web. Worried about
information overload, or about finding anything, or about being found? AltaVista
Search at http://www.altavista.digital.com will find any Web page for you.
"Knowbots" -- a technology of knowledge-seeking robots that scour
the Web locating information to answer a question you posed -- are just
over the horizon. Worried about quality? Look for Magellan 3-start and 4-star
sites and watch for other organizations to issue their own seals of approval.
George Gilder describes as the "law of the telecosm" the phenomenon
that network bandwidth is following computer chips into being so cheap as
to be wasteable, pushing computing power away from centralized locations
into the hands of individuals. The Clinton administration has been pushing
hard to make the Internet hospitable for business, sometimes running afoul
of the cowboys and vigilantes who have come to believe that no laws should
apply in cyberspace. By pushing for the Internet in every classroom, the
Clinton administration is guaranteeing a new generation of networking-literate
young adults. There is no turning back the clock on Internet.
Most of those companies cited by O'Reilly have used the Web only for publications
such as catalogs, brochures, and bug fixes. Those who invite customers to
order electronically find most customers are wary of paying by Internet.
A growing number are experimenting with "intranets" -- private
company networks embedded in the Internet, using full Internet tool sets,
but sealed off from casual access behind firewalls. They still do not dare
to place proprietary information on servers attached to Internet, for they
rightly fear for the theft of their information. Few companies have begun
to use these tools for full-scale business operations within the Internet.
They have good reasons.
The Darker Side
As soon as a company starts to look into the engineering, social, and legal
problems associated with electronic commerce, it is likely to uncover a
host of vexing problems for which no good solutions yet exist. A list of
the most important appears below. All the items on this list exhibit an
interplay between social and business practice and the technology. The ones
stated first have the strongest technology components.
1) Web an open publication medium. The protocols of the World Wide
Web are designed for people who want to freely publish and distribute information.
The server on your host that interfaces the Internet to your computer can
read any directory not marked private by its owner. All the files you want
to publish on the Web must be marked world readable. Files you don't want
to publish but which must be used by your Web browser -- such as files of
passwords for access to certain Web pages -- must also be world readable!
These design assumptions are incompatible with the private company intranet,
which is part of the reason that implementing secure intranets using Web
technology has been so difficult.
2) Security vulnerabilities. The popular Netscape browser has been
the subject of a stream of official security advisories. In 1995, the encryption
algorithm (used to protect credit card numbers during a financial transaction)
was found to be crackable; Netscape quickly issued a patch. Netscape allows
you to download automatically, from another Web site, programs in the Java
language -- but as of March 1996 does not let you prevent that program either
from reading any of your files and sending their contents to someone on
another web site, or from installing Trojan horse files on your computer.
Netscape aside, many local computer access controls can be subverted if
another machine can pretend to have the Internet address of a machine you
trust (a problem called "IP address spoofing"). Most email systems
can be tricked into showing a return address different from the actual sender.
There are packages of "Internet burglar tools" regularly used
by crackers to cover their tracks and create trap doors to expedite their
future re-entries.
3) Encryption. Modern encryption technology offers a host of protocols
from authentication to privacy. Very few people routinely use these technologies.
Companies that use them to protect proprietary data can quickly find themselves
in deep trouble if they lose the encryption keys; they are turning to key
escrow systems as a means of retrieving copies of the keys in case of emergencies.
Privacy advocates are challenging key escrow systems because they fear that
the government (or the companies) can obtain keys illicitly and listen in
on private conversations. Law enforcement agencies are worried that encryption
will cut off their ability to legally wiretap conversations between suspected
criminals; however, government attempts to regulate encryption create sharp
conflicts with privacy advocates.
4) Signatures and certifications of documents. There are cryptographic
protocols to sign email, documents, and files unforgeably; with digital
signatures, any recipient can quickly tell whether the document has been
tampered with or validate whether you are the author. There is still little
legal precedent and business practice for electronically signed documents.
5) Viruses. It is easy for a virus to enter your computer surreptitiously
on a floppy disk you had briefly inserted into another computer. When activated,
the virus can infect other programs and floppy disks and can set off logic
bombs that damage your files long after the infection. More recently, a
new feature of Microsoft Word 6.0 -- the automatic macro -- can transmit
viruses in ordinary documents that most virus checkers don't scan.
6) Privacy concerns. New practices enabled by the Internet are being
taken as privacy threats by many consumers. There was a furor in 1995 when
it was discovered that Windows 95 electronic registration form sent system
configuration information to Microsoft without telling the user. Many users
are incensed that many Web sites automatically monitor and log the addresses
of those who visited them. As noted above, downloaded Java programs can
send directory listings from your machine back to their authors and can
often install new files without your knowledge.
7) Disregard for copyrights, licenses, and intellectual property.
Because it is so easy and cheap to copy data in the Internet, many people
routinely copy and distribute files, including licensed software, without
permission of the author. Protocols for "transcopyright" -- automatic
transfer of copyright on payment of a penny or two -- are widely discussed
but are not implemented. A recent proposal by the Clinton administration
to extend existing copyright law to the Internet has been fiercely opposed
by groups who think that large corporations will be the primary beneficiaries,
and who want to preserve the lassez-faire copying practices of the Internet.
8) Frauds. It is easy to "spoof" an email return address
-- i.e., make the from field on an email you sent look like it actually
came from someone else. This flaw in the mailer protocols is frequently
used by pranksters to impersonate the boss, the president, or others whom
they are trying to embarrass. It is also used by harrassers to hide their
identities.
9) Spamming. A user can flood a site with thousands of messages,
or can blanket a large mailing list with a single message. In a recent incident,
someone spammed thousands of LISTSERVs -- servers that automatically manage
discussion groups -- by subscribing third parties without their knowledge.
Those victims started receiving hundreds of unwanted messages a day and
had considerable difficulty unsubscribing from all those LISTSERVs.
10) Gullibility. We live in an age when many people are (paradoxically)
cynical and gullible at the same time. They will spread rumors like wildfire
through bulletin boards, newsgroups, email, and Web sites -- without checking
or even questioning validity. Many companies fear being put out of business
by packs of "Internet wolves" who believe an allegation and undertake
their own retalitory action.
11) Internet cowboys and vigilantes. There is a surprisingly large
number of Internet denizens who believe that laws ought not to apply in
cyberspace. They perform acts of fraud (which they call harmless pranks)
and sometimes take further actions against those whom they dislike, such
as spamming, badmouthing in newsgroups, making harrassing phone calls in
the middle of the night, or breaking into their systems. Because of the
ease with which one can hide identities in the Internet, few of these people
ever get caught.
12) Tax policies. Many jurisdictions collect sales taxes and income
taxes on transactions involving their residents or merchants. It is an open
question how this will be carried over to the Internet when parties to the
transaction are anonymous or when the transaction did not happen in a locality.
Some people are saying that in the future of the Internet, taxes will be
voluntary.
13) Law enforcement. Modern law enforcement is based on jurisdictions
-- local authorities who will prosecute local infractions. It is still an
open question how to deal with the Internet, where there is often no well-defined
jurisdiction. In a recent case, a resident of Tennessee successfully prosecuted
a Web site proprietor in California for making pornographic materials available
on a Web site that the Tennessean downloaded, in violation of Tennessee
law.
Complexity of Information Systems
These practical issues of operating a business in the Internet generate
many complexities and uncertainties not apparent to the casual observer
of the "promises of electronic commerce." No wonder people get
discouraged and want to wait until some of the problems are solved before
betting their firm on the Internet.
The problem of implementation complexity bears many similarities to an older
problem that organizations have faced for two decades: how to realize a
return on investment on information technology. Against a history of poor
progess toward improved workplace productivity, technologies such as Internet
and Java show up as possible silver bullets whose glitter attracts public
attention. But the question is still the same: how come we've invested in
all that information technology but only have 0 - 1.5% annual productivity
improvement to show for it over the past two decades? From the engineer's
standpoint, the reason is the complexity of the client-server systems that
have been used to automate existing practice; although it's clear we've
automated inefficient processes, it's not clear either how to make those
processes more efficient and how to coordinate databases, clients, software
applications, and Internet access. This is where many groups sink into a
fog and can't figure out what to do next.
The Internet doesn't solve the problem, it worsens it. There are more kinds
of breakdowns that can occur. The Internet's current focus on information
exchange and publishing, rather than coordination, creates a wider gap between
Internet technologies and business process than exists between office systems
and business processes. DARPA (the Defense Advanced Research Projects Agency)
still considers it a research problem to devise technologies to support
collaborative work and the processes of commerce in the Internet.
Designing for Coordination
The current common sense about the marketplace inclines us to think of commerce
as a game of competition between buyers and sellers. It is an information-exchange
game featuring sellers publishing advertisements for buyers, buyers transmitting
orders and payments to sellers, third parties distributing goods and services
from sellers to buyers, and strong competitors knocking off the weak. The
role of the technology is to transmit the relevant information at the various
stages of the game.
The information view of commerce and Internet has been useful as far as
it goes. It has given us many technologies from email to the Web browser.
But this view does not lead to many technologies that support human coordination.
Human acts of coordination do not appear as information transfers and are
not well served by existing Internet technologies. Put another way, the
complexities of making information systems that support business and commerce
arise from the lack of an overall map of the coordinations that the information
technology is supposed to support. What we need is a way ot interpreting
commerce -- a new common sense -- that makes the coordination explicit and
brings it to the center of the design process.
Let us begin by reframing commerce as a game of exchange transactions. Buyers
and sellers engage in transactions to produce mutual value. Their transactions
involve much more than transfers of information -- they involve acts of
coordination such as requests, promises, agreements, satisfaction, and dissatisfaction;
and consequences of past history of transactions on assessments of quality,
trust, and credibility. I suggest that a coordination-centered view of commerce
will allow us to design technologies that pierce the fog of complexity.
The first question is, what is the (universal) nature of the coordination
in commerce? The answer to this question is found in the linguistic structure
of the exchange transction and their interconnections as business processes.
The second question is, what kinds of technologies do we need to support
that coordination and avoid the breakdowns?
The Exchange Transaction
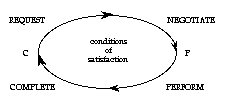 The molecular building block of commerce is the exchange transaction. In
this transaction two parties, C and P, agree to and fulfill mutual conditions
of satisfaction. The first party, C, is usually called the customer or buyer;
the second party, P, is usually called the performer or seller. P accepts
C's request to provide something for C, in exchange for which C will provide
a payment to P. The transction can be visualized as a cycle of four parts:
The molecular building block of commerce is the exchange transaction. In
this transaction two parties, C and P, agree to and fulfill mutual conditions
of satisfaction. The first party, C, is usually called the customer or buyer;
the second party, P, is usually called the performer or seller. P accepts
C's request to provide something for C, in exchange for which C will provide
a payment to P. The transction can be visualized as a cycle of four parts:
1) Request: C makes a request of P to provide the service. (Often
this amounts to taking P up on an offer P has made.)
2) Negotiation: C and P come to an agreement on exactly what will
be provided (C's condition of satisfaction) and what payment will be made
(P's condition of satisfaction).
3) Performance: P carries out the actions needed to fulfill his part
of the bargain and notifies C when he is done.
4) Settlement: C accepts P's work, declares it satisfactory, and
pays.
These four segments of transaction are observable by the speech acts that
mark them: C says "I request" in part 1; P says "I agree"
in part 2; P says "I am done" in part 3; and C says "I am
satisfied" in part 4. The speech acts permit an observer (who may be
a machine) to notice when a transaction is changing state. They give a rigorous
basis to track a transaction toward completion.
This is the model devised by Fernando Flores and Terry Winograd to describe
transactions. It has been called ActionWorkflow in the business-process
management systems of Action Technologies, Inc. The same model they invented
for business processes describes commerce. Workflow can be used to map recurrent
commercial processes and support them through technology.
When two people do business "face to face", it is easy for them
to track the transaction and tell that it is moving toward completion. But
when they are separated by a distance and connected by (say) an Internet
connection, there are many opportunities for a breakdown in the loop:
1) Communication breakdowns. Loss or corruption of an email, file,
document, or form anywhere in the transaction; these objects convey speech
acts or record declarations to be fulfilled in the future.
2) Request breakdowns. The format used by C to convey the request
is not recognized by P. C does not make a clear request, e.g., C's hint
or suggestion was not perceived by P as a request.
3) Negotiation breakdowns. P ignores C's request. P says he agrees
to C's conditions when he does not mean to. C and P have different understandings
of what was agreed to. Either C or P lets a negotiation drop without acknowledgement.
4) Performance breakdowns. P does not complete on time. P does not
fufill the agreed conditions. P performs shabby work. P stops work without
informing C. C decides he does not want the job done after all but does
not inform P.
5) Settlement breakdowns. C does not declare satisfaction. P does
not follow up with C. C does not pay. C is dissatisfied and must file a
complaint.
6) Missing-performer breakdowns. C puts the request in an in-basket
over which no one has taken responsibility. C assumes that the firm will
assign a P to work on the task. No one notifies C who P is, even when P
starts work. P is an impostor.
7) Missing-customer breakdowns. B starts doing something for C without
C's having requested it. C is an impostor.
Business Processes
During any segment of a transaction, C or P can make secondary requests
of other people to obtain information or services. For example, suppose
that C needs price information in order to fill out an order form; C's request
to a clerk X initiates a new transction by which X gives C the requested
information. Another example is when P asks for help from another person
Y during the performance segment; in this case, the secondary transaction
has P as customer and Y as performer.
In this way a nonlinear network of transactions can be called into play
in fulfillment of A's original request. That network, called a business
process, accounts for all the people involved in fulfilling a customer request
and the exact conditions of satisfaction each one works toward. The Internet
allows all the participants in a business process to be at different locations,
possibly separated by large distances. It is important for the firm to have
technology that supports them in carrying out the entire process without
breakdown. That means they must have safeguards against each of the coordination
breakdowns listed above.
The ability to refine a transaction by explaining segments as webs of secondary
transactions makes the model hierarchical. We can home in on as fine a level
of detail as necessary by locating anyone else a person must coordinate
with during each stage of a transaction.
Trust
An essential ingredient of the exchange transaction is that the two parties
operate from assessments about each other's trust -- i.e., their competence
to fulfill their part of the bargain and their sincerity in any promises
they make. If either party does not trust the other, the transaction may
fail or won't take place at all. Trust is assumed or is based on statements
of others. It may be built up over a series of transactions, in which case
it leads to repeat business and to word-of-mouth recommendations for more
business.
How does trust work linguistically? We represent the other person by some
kind of symbol and associate our assessments of trust with that symbol.
The symbol may be the person's face or body shape in a face-to-face transaction;
or the person's voice in a telephone transaction; or the person's handwriting
in a fax transaction. As soon as we recognize the face, the voice, or the
signature, we immediately recall the trust we have in the person. In these
everyday cases, we take for granted the reliability of the association between
the symbol and the person on the other side of a transaction. It is conceivable,
but usually unlikely, that a stranger will disguise himself as a trusted
customer in appearance, voice, or handwriting. In the Internet, the only
symbol of the other person is the notoriously unreliable return address
in an email.
Engineers use the term authentication to refer to the problem of associating
a person with a symbol. The symbol is then used to mark roles in transactions.
If this cannot be done reliably, trust in Internet transactions will be
low and commerce will falter.
Encryption is the principal technology that can be used to authenticate
a person or a document authored by a person across a long distance Internet
link. Even if privacy and secrecy were of no concern to anyone, the need
for reliable authentication would drive the development of encryption technology.
It is astonishing that this simple truth about human coordination is missing
from the basic architecture of Internet protocols. If human coordination,
rather than information exchange, had been at the center of attention of
protocol designers, it would be exceedingly difficult today to spoof an
email or Internet address or to forge a signature on a document. Authentication,
rather than secrecy, would be the primary reason for encryption technology.
Technologies in Support of Commerce
The single most important technology for Internet commerce is authentication.
It should be virtually impossible for a person to pretend to be someone
else when logging in to a system. It should be virtually impossible for
a third party to alter email addresses, digital signatures, or the content
of any document without detection. It should be virtually impossible for
someone to fake the Internet address of a computer when connecting to another
computer in the Internet. These technologies are known, they just are not
used much in practice. I think this is because designers have tended to
see the role of the Internet as a conveyor of information rather than a
facilitator of coordination; consequently they paid more attention to encryption
as a source of secrecy.
As the next most important group of technologies for commerce, I put those
that facilitate coordination. These usually are grouped under the heading
of workflow systems, cooperative work systems, conversation-tracking email
systems, or coordination systems. Their purpose is always to enable the
participants in transactions or business processes to know exactly the state
of the transaction at any given moment and how far from completion it is.
The same technologies can enable data collection that can be used to guide
future process improvements. These technologies are inttimately related
to the firm's ability to deliver customer satisfaction and guarantee quality
at every stage of a process.
Third, I put techologies for payments. Without them half of most exchange
transactions could not be successfully implemented. I place them third because
without authentication and coordination payments would not be possible.
Fourth, I put technologies that ensure the integrity of the Internet itself,
the medium for all transactions. These include technologies for detecting
criminal acts, resisting viruses, and recovering from computer and connection
failures.
Fifth, I put technologies that support particular kinds of transactions
such as financial, order-entry, sales, and other applications. These technologies
are built on top of the others mentioned above and directly support the
practices of people operating in various domains.
Conclusions
The model of coordination systems provides the night vision needed to pierce
the fog. Workflow mapping helps the information system engineers, and the
workers themselves, to see how to select software application packages needed
to match their practices, how to see the overall process, how to see where
information systems couple with people, and how to measure the coordination
taking place throughout the organization. Workflow management systems, which
can coordinate all the system elements and people they need in their processes,
will be especially important to maintain customer satisfaction and service
quality at every step of the way.
 The molecular building block of commerce is the exchange transaction. In
this transaction two parties, C and P, agree to and fulfill mutual conditions
of satisfaction. The first party, C, is usually called the customer or buyer;
the second party, P, is usually called the performer or seller. P accepts
C's request to provide something for C, in exchange for which C will provide
a payment to P. The transction can be visualized as a cycle of four parts:
The molecular building block of commerce is the exchange transaction. In
this transaction two parties, C and P, agree to and fulfill mutual conditions
of satisfaction. The first party, C, is usually called the customer or buyer;
the second party, P, is usually called the performer or seller. P accepts
C's request to provide something for C, in exchange for which C will provide
a payment to P. The transction can be visualized as a cycle of four parts: